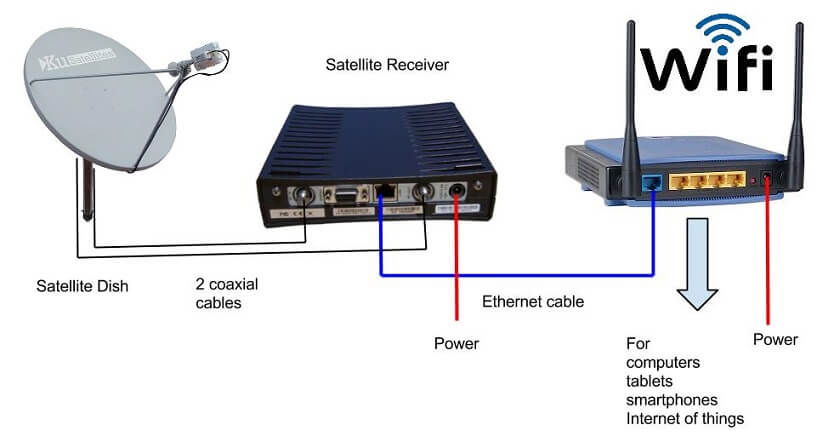
Hack your network
Data: 1.09.2018 / Rating: 4.7 / Views: 770Gallery of Video:
Gallery of Images:
Hack your network
i only acctually hacked it because most videos dont acctually do the hack so it dont work Ryan Russell is the bestselling author of Hack Proofing Your Network: Internet Tradecraft (Syngress Publishing, ISBN: ). He is an Incident Analyst at SecurityFocus, has served as an expert witness on security topics, and has done internal security investigation for a major software vendor. Here we give your some ideas of how to police your environment and to look for signs of malware. Study the hacker threat In order to determine whether your servers or desktops have been hacked, you should study some hacking techniques and learn what the attack vectors are. Accept my apologies, if there is any article already available of my topic in nullbyte please show me the link. If there is not than can you please tell me how to get access of a. This is just a partial screenshot of the output from the nmap network scan, but it does include three IP addresses, . 108 starting about the middle of the screen. Hack Proofing Your Network: Internet Tradecraft points out that statistics are no defense, and that such an attitude is irresponsible. First download the CSploit from here and install in your android phone. Now open your cSploit and select your network and select the target IP which you want to. Attempting to hack into your own wireless network can help you spot potential WiFi security vulnerabilities and figure out ways to protect against them. 15 free (or almost free) WiFi security. There are various ways to browse the internet for free on your network operator. There is no serious hacking skills needed, the only thing is making use. How to hack a computer on a different network? [closed up vote4 down vote favorite. If they detect you, they will block your traffic. If your ISP detects you, they will cancel your service. Finally, what you are asking about is illegal. I don't know where you are, but in the US, it's a felony. It's fine to talk theory, but we're not going. Finding that your computer network has been hacked can feel like having your house burglarized. Hacking is the term used to describe an unauthorized user using a computer or network. Once a network has been hacked, it is evident that the hacker knows. There's been a lot of talk about the recent hacks against the Democratic National Committee and many, many questions and arguments about who was responsible. There are some interesting things. Two Parts: Preparing Before You Hack Hacking Community QA. Start with the basics but make sure you have authorization to attack your target: either attack your own network, ask for written permission, or set up your own laboratory with virtual machines. Attacking a system, no matter its content, is illegal and WILL get you. Locate your network or the network that you have permission to penetration test. Once youve spotted your network on the everpopulating list, hit Ctrl C on your keyboard to stop the process. Note the channel of your target network. Kali Linux is a securityfocused operating system you can run off a CD or USB drive, anywhere. With its security toolkit you can crack WiFi passwords, create fake networks, and test other. Hi all members In this step by step tutorial you will learn about: How to Hack Network Computer using the command prompt. Things to remember CP Command Prompt The WiFi router you use to broadcast a private wireless Internet signal in your home or office is not only easy to hack, says a report released today, but the best way to. Sadly, almost no systems are entirely hack proof but browser security tests 7 Browser Security Tests to Try Out and Prevent Exploit Attacks 7 Browser Security Tests to Try Out and Prevent Exploit Attacks Read More, server safety measures, and network safeguards can make your set. This was a surprise demonstration he gave me last weekend on Hacking Your Cable TV Networks, which he is going to present next week at Hack In The Box (HITB) Security Conference in Amsterdam. Network Security is considered a self taught dark art like lock picking. Just like lock picking, if you want to be good at it go purchase a lock and start picking. Going to your neighbors pad and trying to pick their lock is frowned upon in most court systems. The same with network security, if you. Modern Vehicles all come equipped with a CANBUS Controller Area Network, Instead of having a million wires running back and forth from various devices in your car. While ethical hacking (or white hat hacking) might sound like an oxymoron, its a smart, proactive method that can help prevent malicious hackingattempts by outsiders to break into networks, steal private information, or hold systems for ransom. Your wireless router is a prime target for hackers wanting to infiltrate your network or freeload off your WiFi connection. Here are some things you can do to make your wireless router harder to hack. March 1, 2005; If you plan on reporting this hack to the authorities, you should avoid contacting the ISP at this time. Use a firewall on your network or. While it's still true that hackers who are bent on gaining access to internal networks are a menace, IT managers have also discovered that another type of hacker the ethical hacker is an. Select your network and click Connect, enter your password if necessary, click OK, and then click Connect a second time. Advertisement Now that you're online, let's install Reaver. how to hack your network provider system goto ur command prompt, type the command telnet ipnumber. replace ipnumber with any address e. 2 2) if the ip is up and running, you should see sumthn like REQUESTms, in miliseconds. it will continuosly b scrollin down like a loop at high speed. So you want to hack a computer and you've got Kali linux installed? Then you are on the right place! I am going to show you how to hack a computer. Okay, so I have two people around my home that seem to be accessing my wireless network and using it without my permission. I know that I can just add a password to the wireless or add a Mac address filter in my router. But I want to teach those guys a lesson. I have the information regarding their. In this tiny lab, you will connect your mobile phone to your WiFi as you normally do, and also connect your laptop to your WiFi as your clientsguestcustomer would at your house, waiting room, or lobby at your place of work. 5 Ways To Hack Into Your Neighbor's Wifi Network. Hacking into your neighbor s wifi network may be easier than you think and, conversely, your neighbor may think it s easy to hack into your network. How Do Hackers Hack Your Network? You'll never believe how the world's most effective hackers breach your network security In the world of cybercrime and hacking, youd think that every system breach was the work of a computing genius, buried away in a dusty basement; a hidden mastermind. If someone is smart enough to attempt to hack into your network, hiding your SSID is just going to make them laugh to themselves as they easily figure it out in 5 seconds. wimiadmin Staff answered 3 months ago. A new edition the most popular Hack Proofing book around! IT professionals who want to run secure networks, or build secure software, need to know about the methods of hackers. Anatomy Of A Hack: How A Criminal Might Infiltrate Your Network. Anatomy Of A Hack: How A Criminal Might Infiltrate Your Network. Theft On The Web: Prevent Session Hijacking. Beat Hackers At Their Own Game With A Hackerbasher Site. This article is not intended to show you how to hack something, but rather to show how attackers. The hack uses the network interchange service called Signalling System No. 7 (SS7), also known as C7 in the UK or CCSS7 in the US, which acts as a broker between mobile phone networks. Organized gangs of cybercriminals are trying to break into your bank account, steal your identity, or take control of your home network to send spam and launch attacks against other machines. Ever wanted to show all your friends at school who's boss? You're in the right place: this video will show you how easy it is to hack into your school's network and play funny pranks on your. The speed of your network connection doesnt just depend on the speed of your hardware. Windows is an operating system that is designed to work on a variety of different hardware and network setups. Street broke into the branch office of a national bank in May of last year, the branch manager could not have been more helpful. Dressed like a technician, Street walked in and said. in your new password use capital and lower letters with number do not use any dictionnary word, also check it could be someone around you that have your password and could connect to the network. Hacking into your neighbors wifi network may be easier than you thinkand, conversely, your neighbor may think its easy to hack into your network. Considering that the police are going to blame you for any activity which happens on your Internet connection This video tutorial is in the Computers Programming category which will show you how to hack a wireless network with WEP encryption. This video is intended only as a means of testing the security of your own network. To crack a network you need to have the right kind of WiFi adapter in your computer, one that supports packet injection. You need to be comfortable with the command line and have a. Your computer tries to get the names of the computers attached to the network with by issuing command to NetBIOS. NetBIOS gives the name of the computers that have been registered. In short NetBIOS gives the various information of the computers on a network. Introduction Ok, I am going to show you a way you can hack the facebook accounts of all the people who are on your network (LANwifi ). This is really the best way to hack facebook accounts. Its much easier than installing RATs, Keyloggers or making phishing sites. How to Get Faster Internet Speed Using DNS Hack. July 13, 2017 returns its corresponding IP address when requested by your computer (client). The DNS has a network of its own i. Network World Attempting to hack into your own wireless network can help you spot potential WiFi security vulnerabilities and figure out ways to protect against them. In order to recover from a hack, you first need to isolate your computer so that the hacker can't continue to control it or use it to attack other computers (especially, if it has become part of a botnet). You should physically disconnect your computer from the Internet.
Related Images:
- Contact Lenses Procedures And Techniques 2e
- Kaplan USMLE Step 1
- Todo Sobre La Tecnica de La Aerografia
- Ian dury album
- Non communicable diseases cdc
- Downton abbey season 1 720p
- Wanted scegli il tuo destino
- Pirates of the carribean dead mans chest
- La bible du score IAE Message Admissions 2016
- Donald e demaray introduccion a la biblia
- The Fault in Our Stars sub nl
- Grammar in use intermediate
- Sing la la la
- Rolling stones grr
- Client list asap
- Satomi yuria satomi yuria
- 1080p after earth
- World radio tv
- Rsmeans Heavy Construction Cost Data
- The dark knight part 1
- Song mkv 1080p
- The Voice S07E04
- Behind the can
- Basic algebra i by nathan jacobson
- Depression Other Magic Tricks
- Hack tol
- Andre 3000 class of 3000
- Fifa 2 13
- Easy French StepbyStep
- The potbelleez junkyard
- TurboC
- Schaums Outline of Investments
- Cat 262d skid steer manual
- Mr and mrs smith avi
- Ethics In Accounting A Decision Making Approach
- Narco terror reloaded
- Hitchhikers guide radio
- Bangin the bosss wife
- Armin top 20
- Home The House Imp
- Winxp sp3 final
- O primeiro beijo clarice lispector pdf
- Episodes episodes 1
- The Beatles I Want to Hold Your Hand
- DVDFAB 10 Crack torrent
- Strap it on
- Because Of Winn Dixie Vocabulary
- Telecharger cours ssiap 1 pdf
- The sims 4 skidrow crack only
- Io confesso ita
- The new normal s01e07
- Dead snow dubbed
- The suit season 4
- Applehda Patcher
- Flashforward season 1 episode 1
- Corel after shot pro 2
- Ebook denis avey
- U2 how to dismantle
- 2005 Deville Service And Repair Manuals
- Captain america soldier hin
- Believe Me A Memoir of Love Death and Jazz Chickens
- Negocios de guerra
- Naruto shippuuden 297
- E type jaguar
- Passion hd garden
- Captain America The Winter Soldier
- Hercule and love affair
- Natalie monroe new
- Magicjack Softphone For Pc
- Sunset strip 2000
- Ymca Yarmouth
- Spanish latin american
- Stomp out loud dvd
- Ccl mumbai heroes theme song
- Froth on the daydream by Boris Vian
- Le monde magique
- Nba open court
- Service For Servicar Harley Davidson
- Typhoon white lighter
- Kid n Play
- F350 Power Sliding Rear Window Wire Harness
- Classic Readings In Cultural Anthropology
- Hart of dixie
- Android file manager
- In paradise nl subs
- Drum it apster
- Happy new year man
- The mann torrent